Here is the easy guide how to setup HCL Domino TOTP on a Domino V12.0.2 server with internet site document.
A. What are the prerequisites for TOTP authentication?
1. Because the TOTP is Time-based, the server needs to have the most correct time for your timezone.
2. The site you are setting up for TOTP must have a TLS certificate
3. Authenticates users must reside in the IDVault
4. Server must have temp. access to the certifier you choose (O or OU where the users are registered in). I choose my O= certifier
5. Check internet password. Or “in vault” or “vault first, then directory”. Both options are good for TOTP.

6. All databases you need must be in V12.0.2 design
B. Configuration TOTP authentication
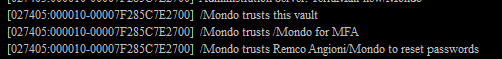
Add MFA key to server and vault:
mfamgmt create trustcert <Your OU= or O=> <certifier> <certifier password>
My example:
mfamgmt create trustcert “*/O=MONDO” cert-o.id <certifier password>
You can check it to look inside you certificates in Domino names.nsf
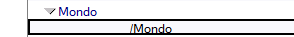
You also have to check the IDVault: show idvault
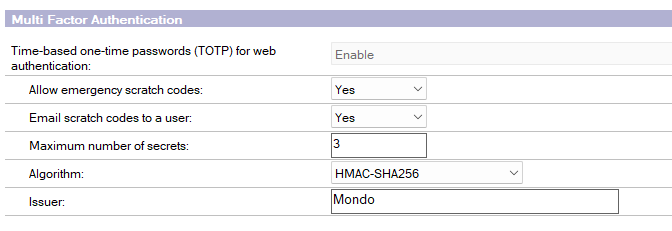
Add TOTP in configuration document
Goto your configuration document linked to your Domino server where you need to enable TOTP for.
Goto the Security tab and enable TOTP.
Enable TOTP on a Internet Site document
Open your corresponding Internet Site document.
In Configuration Tab select TOPT in Enables services:

In Domino Web engine tab, set Session Authentication to “Single Server” or “Multiple Servers (SSO)”
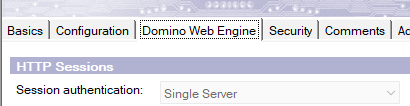
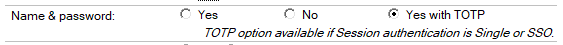
In the Security tab, set Name & password to “Yes with TOTP” in sections “TCP Authentication” and “TLS Authentication”
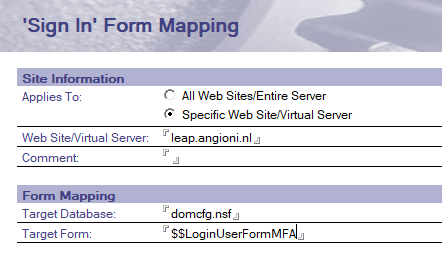
C. Change loginform to MFA login form for sites using MFA.
Open domcfg.nsf and add ( or edit ) the URL you have to enable TOTP for.
Create a Sign In form and choose for the $$LoginUserFormMFA
D. Restart Vault- and Web server(s)
You need to restart ALL servers concerning the IDVault and where the URL lands on (Domino webserver)
And now…. TOTP is enabled and users must login with 2FA. I personally use the Google Authenticator for it.
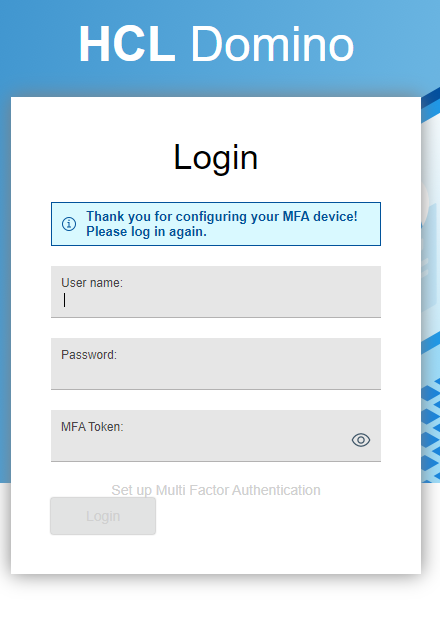
Login without MFA Token
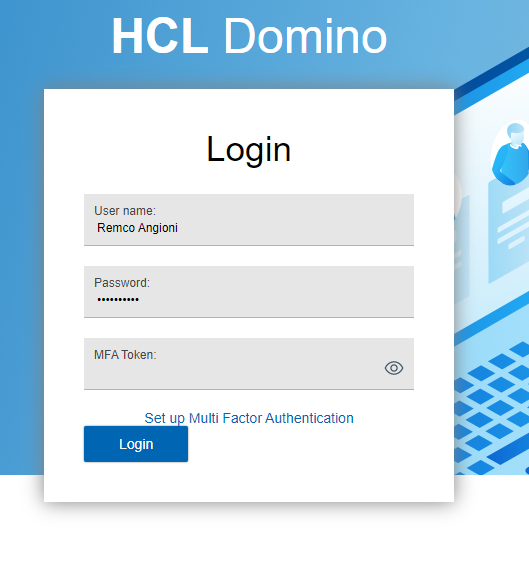
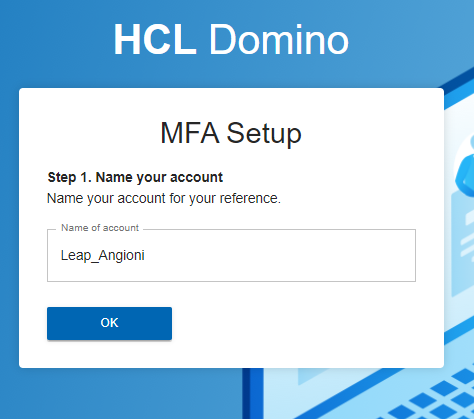
Domino needs to setup MFA on your account
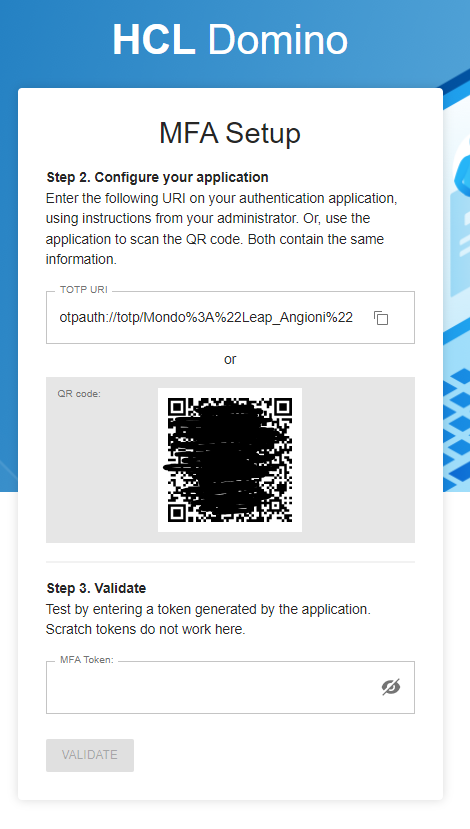
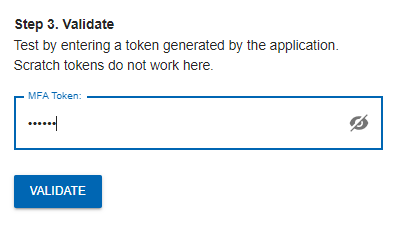
Scan the QRCode with Google Authenticator.
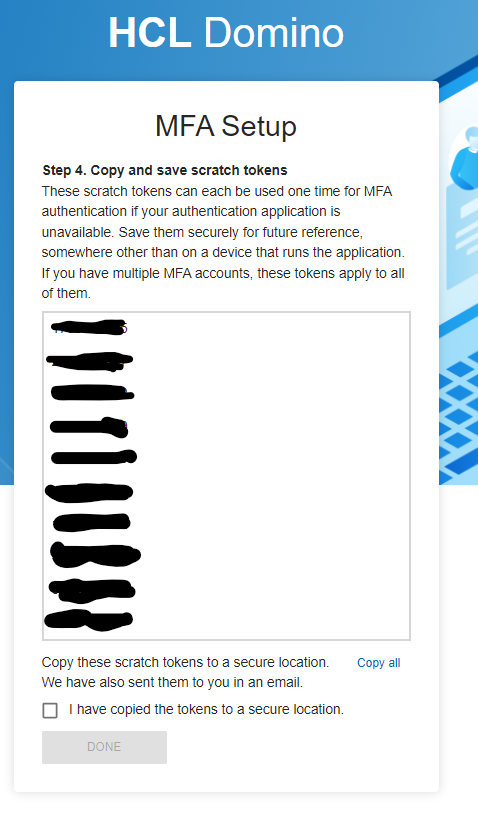
You receive scratch tokens for situations when Google Authenticator cannot be used.
Now 2FA is up and running for you and this URL.
Visits: 750