Intel just forgot to review the security of their firmware
by Volker Weber
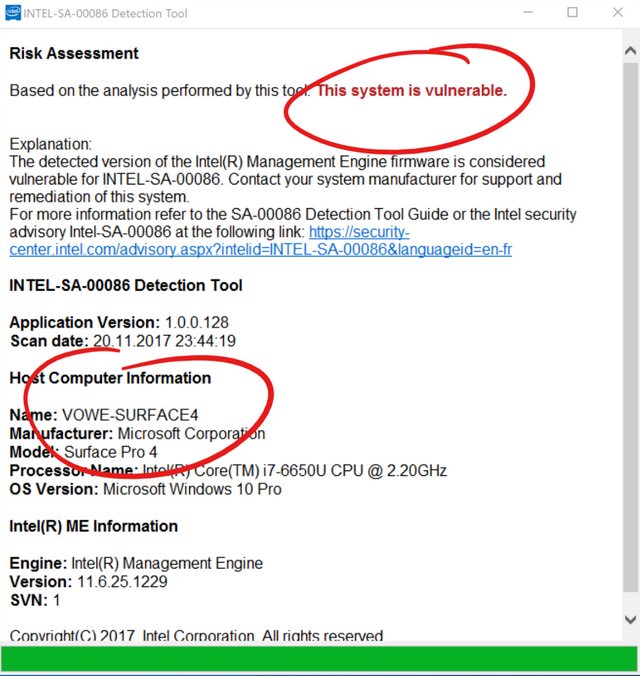
In response to issues identified by external researchers, Intel has performed an in-depth comprehensive security review of its Intel Management Engine (ME), Intel Trusted Execution Engine (TXE), and Intel Server Platform Services (SPS) with the objective of enhancing firmware resilience.
As a result, Intel has identified several security vulnerabilities that could potentially place impacted platforms at risk. Systems using ME Firmware versions 11.0/11.5/11.6/11.7/11.10/11.20, SPS Firmware version 4.0, and TXE version 3.0 are impacted
Comments
Which of the Cs applies here?
- collusion
- conspiracy
- inCompetence
[insert name I fogot]'s razor: never presume malice where incompetence suffices to explain
They also forgot to review the grammar of their security tool interface: "is considered vulnerable for (sic)"
Perhaps to be expected when one sees this sort of gibberish: "The INTEL-SA-00086 Detection Tool will assist with detection of the security vulnerability". Surely the tool's purpose is to perform the detection, rather than assist with the detection?
Occam's Razor points to the third 'C'.
... has performed an in-depth comprehensive security review of ...
A "little" bit too late, this review. This must be done before putting bazillion systems into danger...
In this case, it isn't Occam's Razor, but Hanlon's Razor. Thanks for the heads-up, I just patched my P50.
btw. I was able to update my Thinkpad X240.

